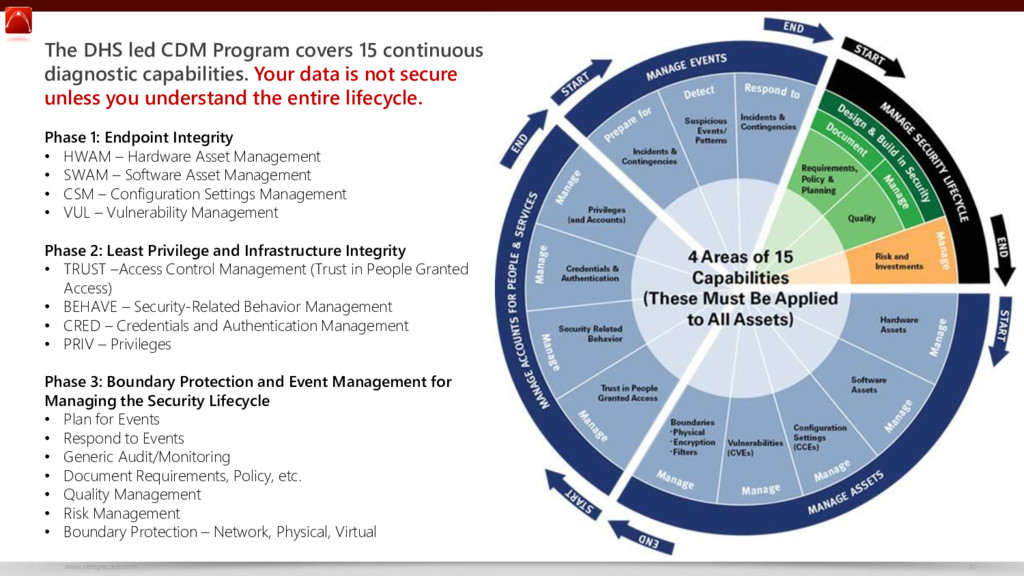
Base editing with high efficiency in allotetraploid oilseed rape by A3A‐PBE system - Cheng - 2021 - Plant Biotechnology Journal - Wiley Online Library

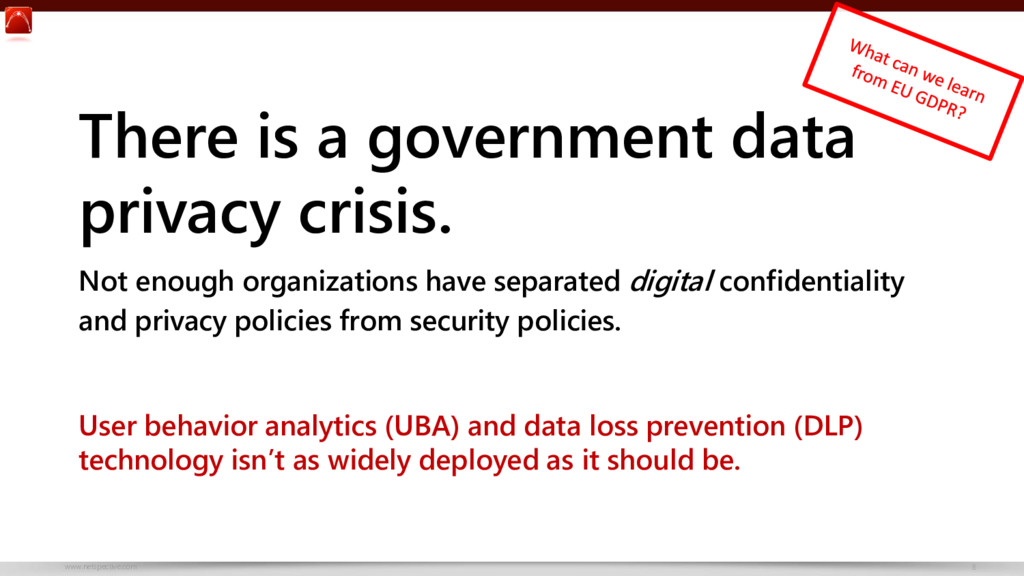
PDF) Information Sensitivity Typology: Mapping the Degree and Type of Risk Consumers Perceive in Personal Data Sharing

Base editing with high efficiency in allotetraploid oilseed rape by A3A‐PBE system - Cheng - 2021 - Plant Biotechnology Journal - Wiley Online Library
CSSI Element: Data: Integrating Human and Machine for Post-Disaster Visual Data Analytics: A Modern Media-Oriented Approach

PDF) Information Sensitivity Typology: Mapping the Degree and Type of Risk Consumers Perceive in Personal Data Sharing
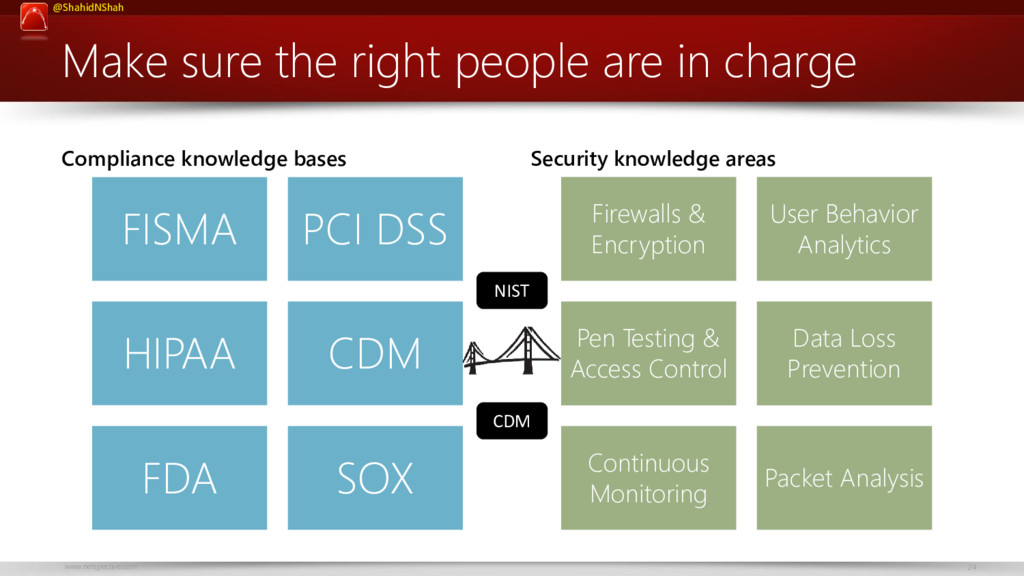
Towards an Economic Cyber Loss Index for Parametric Cover Based on IT Security Indicator: A Preliminary Analysis